CRISPER™
Unified Security Solution
CRISPER™
Unified Security Solution
Unified Cybersecurity, Simplified
Powerful protection, intelligent threat detection, and seamless incident response—all in one platform.
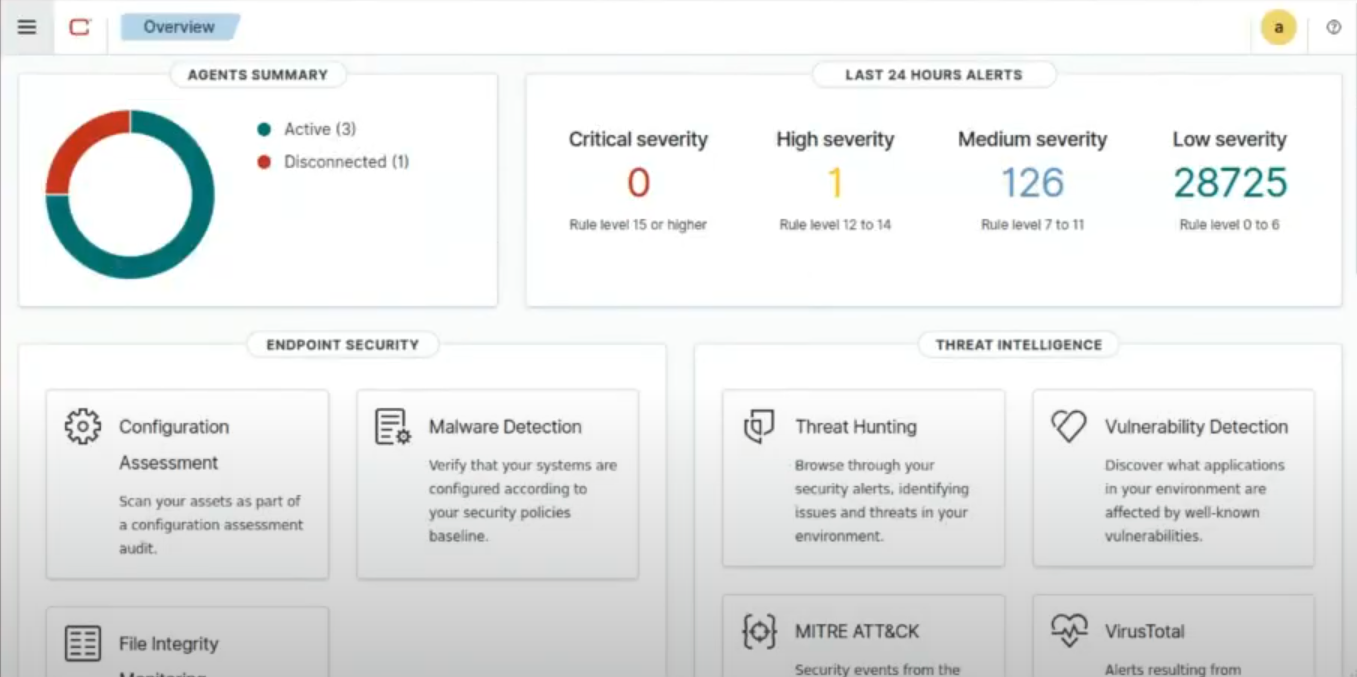
Unified, Flexible, Future-ready Defense
Streamlined Protection for Every Threat
Real-Time Threat Detection
Detect and respond to security incidents with swift, centralized threat management.
Comprehensive Compliance Coverage
Meet industry regulations efficiently with continuous scanning for misconfigurations and vulnerabilities.
Cloud and On-Premise Flexibility
Seamlessly handle security operations of any scale across hybrid, cloud, or on-premise environments.
CRISPER™ FEATURES
- CRISPER™ USS integrates various security layers into a unified platform to provide real-time threat detection and incident response.
- Leveraging Wazuh’s powerful log analysis, file integrity monitoring, and vulnerability detection features, CRISPER™ USS ensures swift identification and mitigation of potential threats across endpoints, servers, and cloud environments.
- With CRISPER™ USS, organizations gain centralized monitoring of security events and compliance status. The solution comes equipped with pre-configured compliance modules that address industry standards like PCI-DSS, HIPAA, GDPR, and others.
- CRISPER™ USS helps ensure that regulatory requirements are met efficiently by continuously scanning systems for misconfigurations and vulnerabilities.
- CRISPER™ USS employs Wazuh’s sophisticated intrusion detection system (IDS) to monitor network traffic for abnormal behavior. Using anomaly detection and signature-based methods, CRISPER™ USS can detect attacks, including brute force attempts, port scans, and denial of service (DoS) attacks, and respond in real-time.
- Built on the Wazuh platform, CRISPER™ USS provides unmatched scalability. It can seamlessly handle security operations for businesses of any size, from small enterprises to large-scale infrastructures, without performance bottlenecks.
- The flexible architecture allows it to be deployed in hybrid, multi-cloud, or on-premises environments, adapting to evolving security needs.
- CRISPER™ USS incorporates Wazuh’s FIM capabilities to ensure that critical files, directories, and system binaries remain secure. Any unauthorized modifications or changes are immediately flagged for review, protecting against malicious insiders and malware-based file tampering.
- By leveraging Wazuh’s log analysis engine, CRISPER™ USS collects and parses security event logs from across the organization. The solution can correlate events from multiple sources and provide actionable insights, helping detect complex attack patterns and reducing false positives.
- CRISPER™ USS integrates cloud-native security monitoring to secure cloud infrastructures like AWS, Azure, and Google Cloud. This includes monitoring cloud assets for vulnerabilities, insecure configurations, and compliance drift, ensuring consistent cloud security enforcement.
- CRISPER™ USS uses lightweight agents that are deployed across the IT infrastructure to collect and send security events and data back to the centralized server for processing. This agent-based approach allows for granular monitoring and policy enforcement without overburdening network resources.
- CRISPER™ USS provides automated and manual incident response options. Using Wazuh’s active response capabilities, it can automatically block malicious activities or quarantine compromised systems. Security teams can also create customized response rules based on their specific operational needs.
With CRISPER™, you don't just react to threats—you anticipate and neutralize them. Take command of your endpoint security and build a more resilient defense against cyberattacks.
CRISPER™ goes beyond traditional endpoint security, giving you unprecedented visibility and granular control to safeguard your most vulnerable assets. With CRISPER™, you gain the insights and tools to proactively fortify your defenses and neutralize threats before they can cause harm.

CRISPER™ BENEFITS
CRISPER™ USS unifies threat detection, incident response, and compliance management in a single dashboard, allowing teams to act swiftly and decisively.
By utilizing an open-source foundation (Wazuh), CRISPER™ USS minimizes licensing costs while delivering enterprise-grade security capabilities.
With regular updates to the Wazuh platform, CRISPER™ USS remains at the forefront of threat detection and defense innovations, ensuring evolving cyber threats are effectively addressed.
![]() Gain Unprecedented Visibility and Control Over Your Endpoint Security
Gain Unprecedented Visibility and Control Over Your Endpoint Security
CRISPER™ empowers your organization with a deep understanding of your security posture. Our powerful endpoint scanning engine thoroughly assesses vulnerabilities, compliance, and security configurations, leaving no stone unturned.
![]() Ensure Regulatory Compliance with Confidence
Ensure Regulatory Compliance with Confidence
Pre-loaded regulatory frameworks like NIST 800-53, HIPAA, and GDPR simplify compliance checks. Customize your own policies for organization-specific or industry-specific requirements, ensuring your endpoints meet the highest standards.
![]() Vulnerability Management Made Easy
Vulnerability Management Made Easy
Leveraging the trusted NIST Vulnerability database, CRISPER™ delivers a detailed view of your endpoint vulnerabilities, prioritizing critical CVEs so you can focus your remediation efforts where they matter most.
![]() Harden Your Defenses with Expert Benchmarks
Harden Your Defenses with Expert Benchmarks
CRISPER's security configuration assessments compare your endpoints against CIS benchmarks—the gold standard in configuration hardening. Strengthen your systems based on expert recommendations for optimal protection.
![]() Comprehensive Visibility Through Unified Logging
Comprehensive Visibility Through Unified Logging
CRISPER's UES agents collect logs from your endpoints, while network device logs can be forwarded for complete visibility. These logs are analyzed, enriched, and aggregated within our powerful SIEM, providing context and highlighting potential threats that might otherwise go unnoticed.
![]() Real-Time Threat Detection and Automated Response
Real-Time Threat Detection and Automated Response
Never miss a beat with CRISPER's automated response. Our intelligent system detects and neutralizes threats in real time, instantly deleting malicious files and blocking suspicious connections. As your incident response capabilities mature, CRISPER™ adapts, allowing you to define custom automated actions for even more tailored protection.